There are two ways to authenticate calls to HubSpot's APIs: OAuth, and private app access tokens. Below, learn more about each method and how to include it in your code for authorization.
If you were previously using an API key to authenticate, learn how to migrate to using a private app access token instead.
Please note: integrations designed for multi-customer use or listing on the App Marketplace must be built as an app using HubSpot’s OAuth protocol
To make a request using OAuth when building a public app, include the OAuth access token in the authorization header:
/~curl --header "Authorization: Bearer C4d***sVq"https://api.hubapi.com/crm/v3/objects/contacts?limit=10&archived=falseSimilar to OAuth, to make a request using a private app access token, include the token in the authorization header:
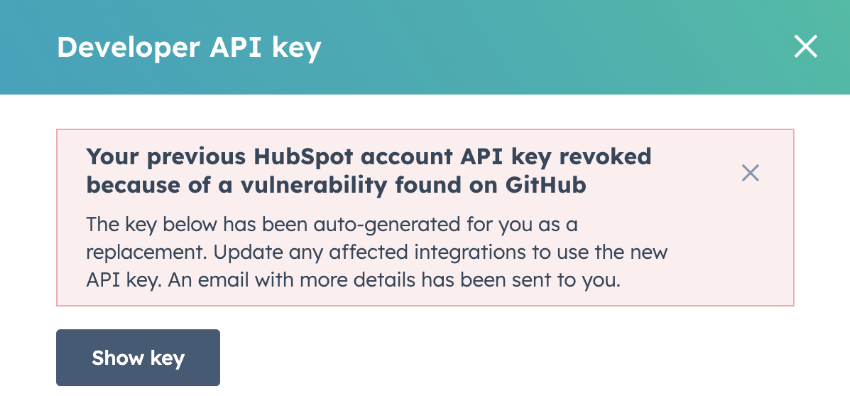
xxxxxxxxxx/~curl --header "Authorization: Bearer ***-***-*********-****-****-****-************"https://api.hubapi.com/crm/v3/objects/contacts?limit=10&archived=falseTo protect developers from potential security incidents, HubSpot leverages the monitoring and secret scanning capabilities provided by GitHub to detect any HubSpot authentication tokens that are publicly exposed in GitHub repositories. Any detected tokens will automatically be deactivated, and you will be notified via email and in-app notification so you can generate a new token and update your integrations to replace the revoked token.
The affected key and token types are listed below:
- Developer API keys created within your app developer account.
- Personal Access Keys used to authenticate commands in the HubSpot CLI.
- Private access tokens used to authenticate requests in a private app.
- SMTP tokens used for sending transactional emails.
The automatic deactivation process will be mandatory on April 7, 2025. If you want to opt-in to this feature proactively, you can opt your account into the beta by following the instructions in this Knowledge Base article.