- Knowledge Base
- Account & Setup
- Account Security
- Set up single sign-on (SSO)
Set up single sign-on (SSO)
Last updated: November 18, 2025
Available with any of the following subscriptions, except where noted:
-
Marketing Hub Professional, Enterprise
-
Sales Hub Professional, Enterprise
-
Service Hub Professional, Enterprise
-
Data Hub Professional, Enterprise
-
Content Hub Professional, Enterprise
-
Smart CRM Professional, Enterprise
-
Commerce Hub Professional, Enterprise
Single sign-on (SSO) allows you to give your team members one account for all of the systems your business uses.
Security Assertion Markup Language, or SAML, is an open standard used for authentication. Based upon the Extensible Markup Language (XML) format, web applications use SAML to transfer authentication data between two parties - the identity provider (IdP) and the service provider (SP).
You can also set up SSO and restrict which login methods users can use to access your account through the login settings wizard. If you have an SAML-based SSO set up, you can require users to log in to HubSpot using their SSO credentials.
General setup
Permissions required Super Admin permissions are required to configure single sign-on.
The SSO setup process should be done by an IT administrator with experience creating applications in your identity provider account.
- Log in to your identity provider account.
- Navigate to your applications.
- Create a new application for HubSpot. To get the Audience URI and Sign on URL, ACS, Recipient, or Redirect values:
-
- In your HubSpot account, click the settings settings icon in the top navigation bar.
- In the left sidebar menu, select Security.
- On the Login tab, if you haven’t configured your portal login settings, click Setup Portal Login Settings. Or, in the Configure single sign-on (SSO) section, click Set up. In the right panel:
- XML upload is available for all SSO set-ups. Drag and drop or click Choose a file to upload your federation metadata. Then, click Verify.
- If you'd like to manually input the data from your identity provider, under the All Other Identity Providers tab, click Copy next to the values as needed. Then, paste the values from your identity provider below. Click Verify.
- If you're using Microsoft AD FS, under the Microsoft AD FS tab, click Copy next to the values as needed. Then, paste the values from your identity provider below. Click Verify.
Please note: If you're using Microsoft Entra (formerly Azure), please use the All Other Identity Providers tab to configure your SSO.
If you're using Active Directory Federation Services, learn more about setting up single sign-on using AD FS.
Require SSO for all users
After setting up SSO, you can require all users to use SSO to log in to HubSpot. This setting is turned on by default.
-
In your HubSpot account, click the settings settings icon in the top navigation bar.
-
In the left sidebar menu, select Security.
-
On the Login tab, in the Configure single sign-on section, select the Require single sign-on checkbox.
/account-security-require-single-sign-on.png?width=700&height=164&name=account-security-require-single-sign-on.png)
Exclude specific users from SSO requirement
After setting up SSO, you can exclude specific users from the SSO requirement to allow them to also log in with their HubSpot user account.
- In your HubSpot account, click the settings settings icon in the top navigation bar.
- In the left sidebar menu, select Security.
- On the Login tab, in the Configure single sign-on section, click Manage exempted users.
/account-security-manage-exempted-users.png?width=700&height=164&name=account-security-manage-exempted-users.png)
- In the dialog box, click the Choose users dropdown menu and select the users that'll be able to log in with their HubSpot accounts. For example, you can select partners and contractors if they lack an SSO login.
- Click Save.
/account-security-select-exempt-users.png?width=500&height=181&name=account-security-select-exempt-users.png)
Please note: the user who toggles the Require Single Sign-on switch on will automatically be added to the excluded users. It's recommended to exclude at least one Super Admin. In the event your identity provider is down, they can log in and toggle the Require Single Sign-on switch off to allow all users to log in with their HubSpot accounts.
Instructions for specific identity providers
Okta
Please note: you need administrative access in your Okta instance. This process is only accessible in the Classic UI in Okta.
- Log in to Okta. Make sure you're in the administrative instance of your Okta developer account.
- Click Applications in the top navigation bar.
- Click Add application.
- Search for HubSpot SAML, then click Add.
- On the General Settings screen, click Done.
- On the application's details page, click the Sign On tab.
- Under the "SAML 2.0 is not configured until you complete the setup instructions" message, click View Setup Instructions. This will open a new tab. Keep it open, then return to the original tab in Okta.
- In the same tab, scroll down to Advanced Sign-on Settings and add your Hub ID in the Portal Id field. Learn how to access your Hub ID.
- Navigate to your user settings. Assign the new app to any users that are also in your HubSpot account, including yourself.
- Return to the View Setup Instructions tab. Copy each of the URLs and the certificate, and paste them in HubSpot in the Identity Provider Identifier or Issuer URL field, the Identity Provider Single Sign-On URL field, and the X.509 Certificate field.
- Click Verify. You’ll be prompted to log in with your Okta account to finish the configuration and save your settings.
- Once your SSO setup has been verified, navigate to https://app.hubspot.com/login/sso and enter your email address. HubSpot will look up your portal's single sign-on configuration and send you to your identity provider to sign in. You’ll also see a Log in with SSO button when visiting a direct link to your account.
OneLogin
Please note: you need administrative access in your OneLogin instance to create a new SAML 2.0 application in OneLogin, as required.
- Log in to OneLogin.
- Navigate to Apps.
- Search for HubSpot.
- Click the app that states "SAML2.0".
- In the upper right, click Save.
- Click the Configuration tab.
- In the HubSpot Account ID field, add your Hub ID. Learn how to access your Hub ID.
- Click the SSO tab.
- Copy the following fields from OneLogin and paste them into the corresponding fields of the SSO setup panel in HubSpot:
-
- Copy the value under Issuer URL and paste it into Identity Provider Identifier or Issuer URL.
- Copy the value under SAML 2.0 Endpoint (HTTP) and paste it into Identity Provider Single Sign-on URL.
- Under X.509 Certificate, click View Details, then copy the certificate, and paste it into X.509 Certificate.
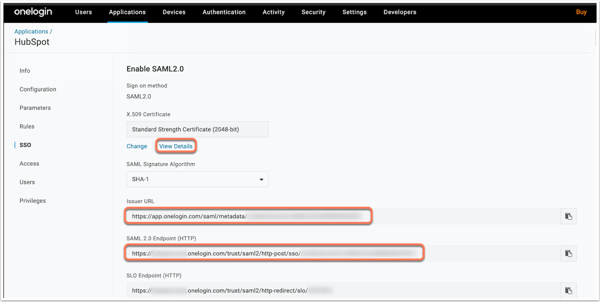
- In the upper right of your OneLogin account, click Save.
Microsoft Entra ID
For Microsoft Entra ID (formerly Azure AD) users, install the HubSpot app in the Microsoft Azure Marketplace and follow Microsoft's instructions to set up the integration. This will allow you to use Microsoft Entra ID to manage user access and turn on single sign-on with HubSpot.
Once your SSO setup has been verified, navigate to https://app.hubspot.com/login/sso and enter your email address. HubSpot will look up your portal's single sign-on configuration and send you to your SSO provider to sign in. You’ll also see a Log in with SSO button when visiting a direct link to your account.
Check out Google's instructions on how you can set up HubSpot single sign-on with G-Suite as your identity provider.
Once your SSO setup has been verified, navigate to https://app.hubspot.com/login/sso and enter your email address. HubSpot will look up your portal's single sign-on configuration and send you to your SSO provider to sign in. You’ll also see a Log in with SSO button when visiting a direct link to your account.
FAQs
Which binding does HubSpot use as an SAML service provider?
HubSpot uses HTTP Post.
I’m using Active Directory Federation Services. What should I use as my relying party trust (RPT)?
Which username format should I set in my SAML application?
HubSpot users are identified by email address. Ensure that your IDP is sending a nameID in email format that corresponds with their HubSpot user’s email address.
Which signing algorithm does HubSpot support?
HubSpot supports only SHA-256 as the signing algorithm. You need to sign your requests with SHA-256.
Which format should I provide my x509 certificate in?
HubSpot requires a PEM format x509 certificate. You should copy the text contents of the PEM file into the x509 certificate field in HubSpot. The value should also include the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE-----.
Can I turn on two-factor authentication, required two-factor authentication, SSO, and required SSO at the same time?
Yes. When you have two-factor authentication turned on, it's active on any login with your HubSpot username and password. Turning on 2FA in HubSpot does not prevent you from logging in using Google's 2FA or SSO. Therefore, if users are excluded from the SSO requirement, you can require HubSpot's 2FA to ensure that any logins that bypass SSO go through 2FA or Google.
If you turn on 2FA for your Google account, this is separate from your HubSpot setup. However, when you log into HubSpot with your Google account, Google's 2FA will protect your HubSpot account.
If you have two-factor authentication and SSO required or turned on in your account at the same time, the following will occur:
- If you're required to log into your account with SSO, you will not be required to also set up 2FA. If you have already set up your 2FA and don't want to be prompted by both the required SSO and 2FA, you can turn off 2FA for your login.
- If your account requires SSO, but you're excluded, you can log in with either 2FA or the Login with Google or Login with Microsoft options.
- If you're required to log in with 2FA and no SSO is set up, you can log in with either 2FA or the Login with Google or Login with Microsoft options.
- If your account has no requirements but has turned on SSO, you can log in with any method including SSO.